AFS on Windows
We provide access to our AFS (Andrew File System) storage using Kerberos authentication tickets and AFS tokens. We recommend accessing AFS through an SCS-provisioned Linux host. For users without an SCS-provisioned Linux host, we offer linux.gp.cs.cmu.edu - our general purpose Linux cluster. If you are using unix.andrew.cmu.edu, you can perform cross-realm authentication to our CS AFS cell cs.cmu.edu.
Software
Windows computers can access AFS remotely on linux.gp.cs.cmu.edu or other supported Linux boxes using the following software stack:
These program installers are provided, hosted and maintained by other organizations and are provided for convenience. See the provided links for additional installation or package information.
- PuTTY (More information can be found at https://www.chiark.greenend.org.uk/~sgtatham/putty/)
- KfW (More information can be found at https://web.mit.edu/kerberos/dist/)
- WinSCP (More information can be found at https://winscp.net/eng/docs/start)
These three programs work with no SCS-specific configuration outside of session details and Kerberos authentication.
Authentication
You will need your SCS Kerberos credentials to authenticate to an SCS Linux host or linux.gp.cs.cmu.edu. For more information on SCS Kerberos authentication, please visit our Kerberos information page. If you are using unix.andrew.cmu.edu, you will need your Andrew credentials and you can then perform cross-realm authentication should you need to reach a volume on our cs.cmu.edu cell.
unix.andrew.cmu.edu users: Please note that if you are using the Andrew unix servers, you will be presented with the Andrew AFS cell as opposed to CS. Please note which cell you are connected to. For more information on the Andrew AFS cell, please visit the Computing Services page on accessing the Andrew FS cell.
Credential Delegation
This change will effectively get a token on login without typing a password on the target Linux host. Alternatively, users can type their Kerberos password when prompted, which will also produce a token. There may be scenarios where delegation is preferred to typing the Kerberos password, such as configuring non-interactive sessions on applicable software.
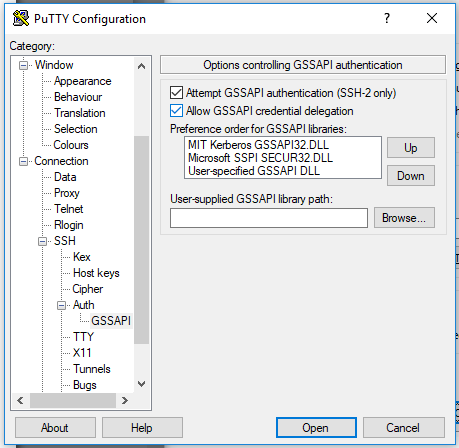
PuTTY: PuTTY has the ability to perform credential delegation. You must be using the latest version of PuTTY (for security and functionality reasons). These options may not apply in previous versions of the software. To delegate credentials in PuTTY:
- It is best to save the session in Putty and apply changes specifically to it.
- Click on the PuTTY Menu Dropdown and select "Change Settings".
- Click on Connection, expand the SSH sub-menu, then expand the Auth sub-menu.
- Select GSSAPI and check the box for ‘Allow GSSAPI Credential Delegation’.
- Ensure you save the Credential Delegation setting specifically to the saved session in Putty (otherwise, it will reset the option every time).
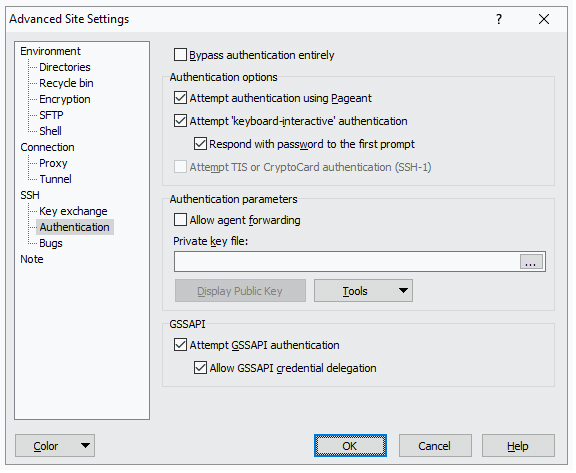
WinSCP: You can enable credential delegation in WinSCP by enabling it as a change to a saved session using the Edit option or at first new login (no saved session). You must be using the latest version of WinSCP (for security and functionality reasons). These options may not apply in previous versions of the software.
-
- If you have a saved session, select the session and click Edit. If you do not have a saved session, create the session for the desired SCS-managed Linux host or desired target host and proceed.
- Click Advanced.
- Under SSH (in the now visible advanced options), select Authentication.
- Check both boxes under GSSAPI section.
- Click OK to finish.
For more information, visit the WinSCP website's authentication page.
Was this page helpful?
Use this box to give us feedback on this webpage and its content. If you need a response, please include your Andrew ID.
Need technical support? Submit a ticket